To insure that your commits are authentic and done by you not by someone else, you need to sign them. One way to do this is using GPG key.
Instructions:
- Install
gpgtool on your operating system (for arch users it's simplysudo pacman -S gnupgfor others you know what to do) - Run
gpg --full-generate-keyIt will interactively ask you some questions: - Choose RSA algorithm
- Choose key size of 4096
- Choose 0 (key doesn't expire option or whatever you find suitable)
- Enter your name
- Enter your email
- Skip the comment section or just write what you want. It will look like this
name (comment) <email@donmain.com> - Type
ofor (O)kay to continue - Enter a passphrase and make sure you will remember it.
gpg --list-secret-keys --keyid-format=longgpg --armor --export YOUR_KEY_ID- YOUR_KEY_ID is the hash in front of
secin previous command. (for example sec 4096R/234FAA343232333 => key id is: 234FAA343232333)
- YOUR_KEY_ID is the hash in front of
- Copy the output certificate and add it to you Github account (Settings > SSH and GPG keys -> New GPG Key) or just follow this link: github.com/settings/keys
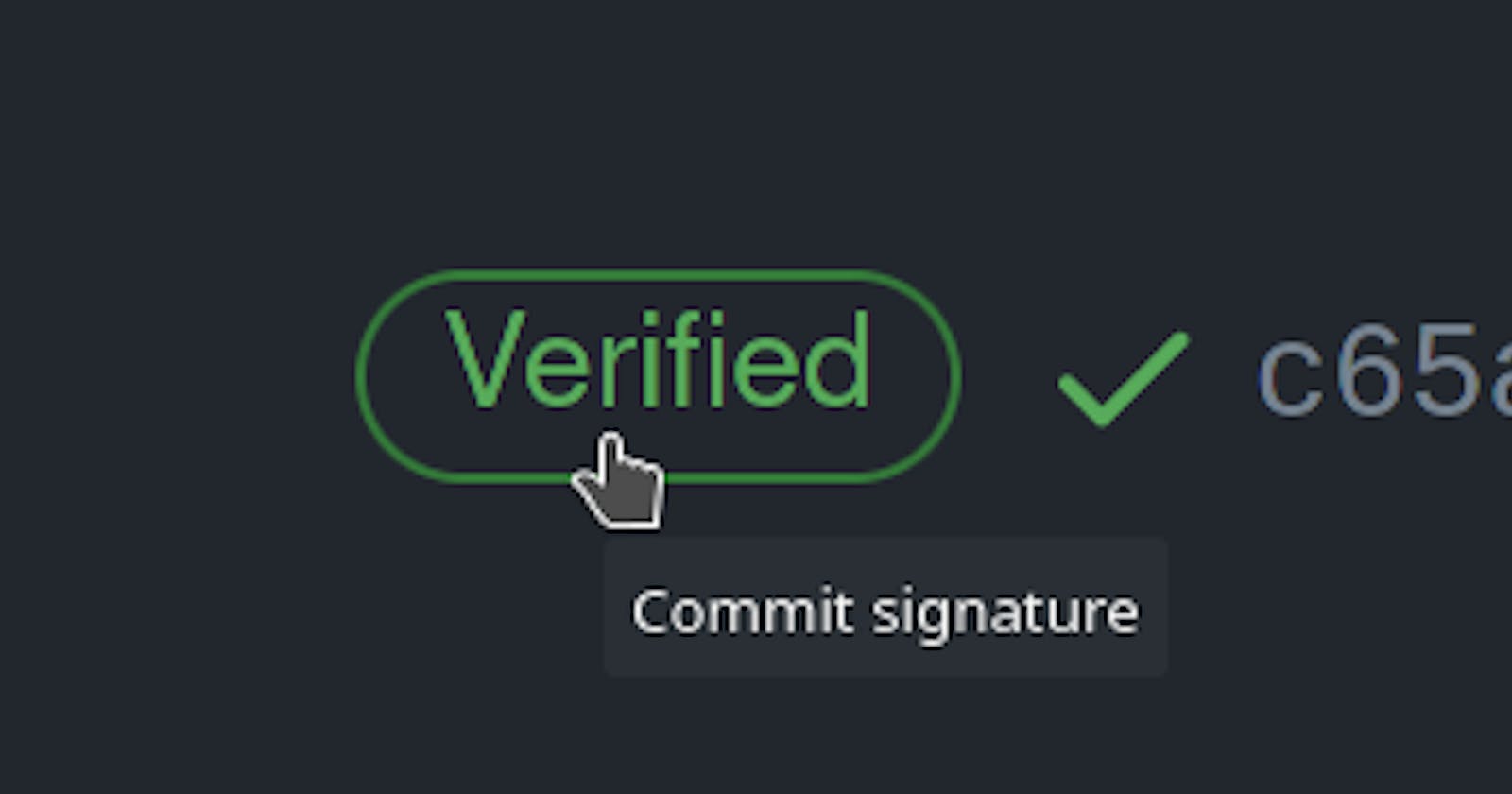
- In the same SSH and GPG keys page mark the checkbox Flag unsigned commits as unverified to make sure all you commits will appear as either verified or unverified** as shown in the picture.

- Now to sign you commits you will have to add the
-Sflag to your git commit command e.ggit commit -S -m "Hello word!" - To avoid adding
-Sto your every commit command make signing the default behavior by runninggit config --global commit.gpgsign true
Done. All future commits made by you, will have the verified icon
Note: It's better to use gpg2 for all previous commands or add an alias for gpg so it points to gpg2
Troubleshooting
- If you are getting this error
error: gpg failed to sign the datathen you might need to add the env varGPG_TTY=$(tty)to your shell profile e.g:export GPG_TTY=$(tty) >> ~/.bash_profile